Introduction to AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is a service offered by Amazon Web Services (AWS) that enables you to securely manage access to AWS services and resources. With IAM, you can create and work with AWS users and groups and assign permissions to allow or deny access to AWS resources.
<a name ="key-components"></a>
Key Components of IAM
IAM has four primary components:
Users: An individual, system, or application that interacts with AWS resources.
Groups: A collection of IAM users. You can assign permissions to a group, and all users in the group inherit those permissions.
Roles: A set of permissions that AWS resources or users can assume.
Policies: JSON documents that define permissions for users, groups, or roles.
<a name="benefits"></a>
Benifits of using IAM
There are several advantages to using IAM for managing access to your AWS resources:
Centralized Access Control: IAM provides a central location for managing user access to AWS services and resources.
Fine-grained permissions: IAM allows you to create custom policies that grant specific licenses, providing precise control over who can access your AWS resources.
Secure access: IAM supports multi-factor authentication (MFA) for added security.
Auditability: IAM enables you to track user activity in your AWS account, making it easier to maintain compliance and detect unauthorized access.
Ease of use: IAM integrates seamlessly with other AWS services, providing a consistent and familiar experience across your AWS environment.
<a name="best-pratices"></a>
Best Practices for Managing IAM
To effectively manage IAM and ensure the security of your AWS environment, follow these best practices:
Follow the principle of least privilege: Grant users only the permissions they need to perform their job functions.
Use IAM groups: Organize users into groups to simplify permission management.
Use IAM roles for cross-account access instead of sharing access keys between accounts.
Enable MFA: Require MFA for all users, especially those with administrative privileges.
Rotate access keys regularly: Change access keys periodically to reduce the risk of unauthorized access.
Use AWS Organizations for centralized management: Use AWS Organizations to manage multiple AWS accounts and apply consistent policies across all accounts.
<a name="setup-guide"></a>
Step-by-Step Guide to Setting Up IAM
Follow these steps to set up IAM in your AWS account:
Sign in to the AWS Management Console: Log in to your AWS account and navigate to the IAM service.
Create an IAM user: Click "Users" and "Add user." Provide a username and select the desired access type (programmatic, console, or both). Configure a password for console access and choose whether to enforce password reset upon the first login.
Assign permissions: On the "Set permissions" page, add the user to an existing group, copy permissions from a current user, or attach policies directly to the user. Click "Next" to review the settings and create the user.
Create IAM groups: Click "Groups" and "Create New Group." Provide a name for the group and attach the desired policies. Add users to the group if needed.
Create IAM roles: Navigate to "Roles" and click "Create role." Select the trusted entity type (e.g., AWS service, another account, or SAML) and configure the trust policy. Attach policies, review the settings, and create the role.
Create custom policies: Click "Policies" and "Create policy." Choose the JSON or visual editor to create your custom policy. Review the procedure and provide a name and description before starting it.
Enable MFA: Select a user from the "Users" list and navigate to the "Security Credentials" tab. Click "Manage" next to "Assigned MFA device" and follow the steps to set up MFA for the user.
IAM Policy Types and Examples
IAM policies can be categorized into the following types:
Identity-based policies: Attached to users, groups, or roles, these policies grant permissions based on the entity's identity.
Example:
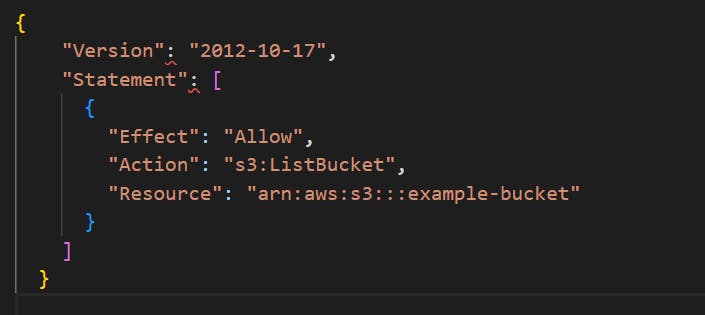
Resource-based policies: Attached to resources, these policies grant permissions based on the actions performed on the help.
Example:
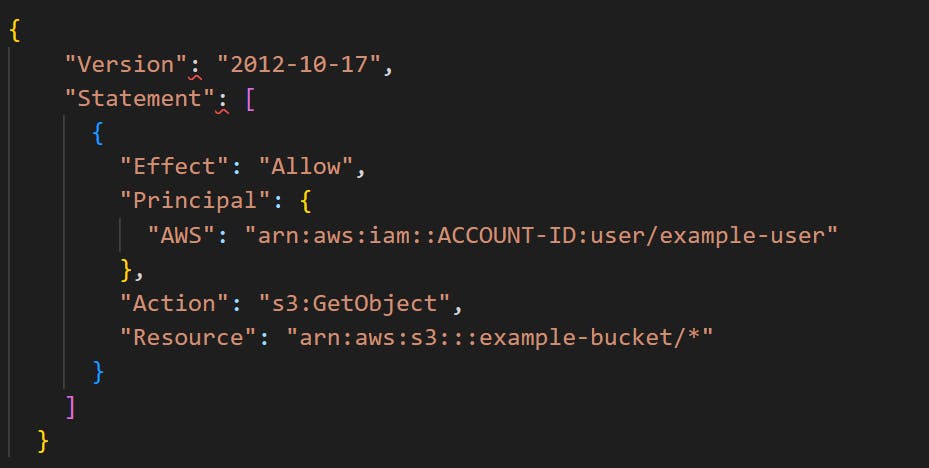
Permissions boundaries: Set the maximum permissions a user or role can have, regardless of the permission granted by other policies.
Example:
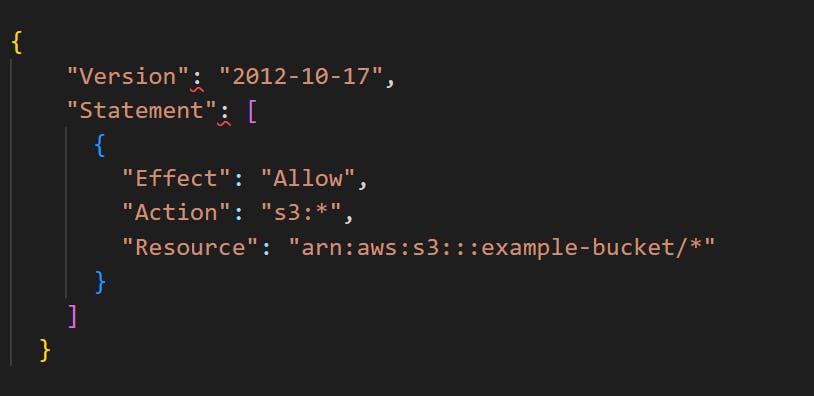
Service Control Policies (SCPs): Apply to all users and roles within an AWS Organization, defining the maximum permissions for the entire organization.
Example:
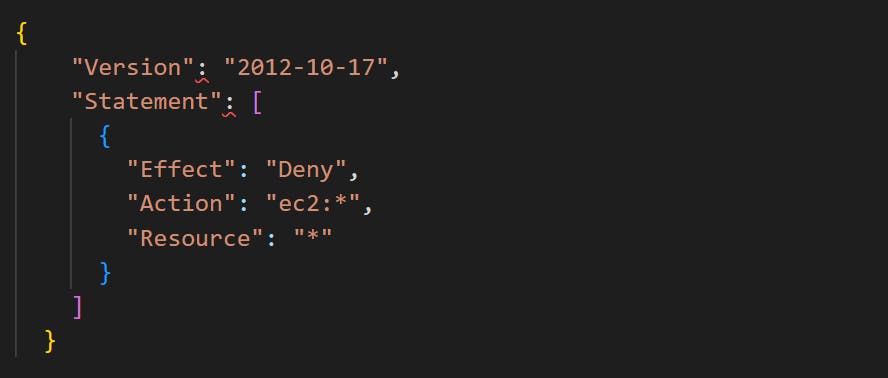
<a name="securing-aws"></a>
Securing Your AWS Environment with IAM
Implement the following strategies to enhance the security of your AWS environment with IAM:
Restrict root account access: Limit the use of the AWS root account and rely on IAM users and roles for daily tasks.
Implement strong password policies: Enforce solid and unique passwords and require regular password rotation for IAM users.
Use roles for applications: Assign IAM roles to applications running on EC2 instances or other AWS resources instead of embedding access keys in the code.
Secure access keys: Store access keys securely and rotate them regularly to reduce the risk of unauthorized access.
Monitor and audit activity: Use AWS CloudTrail and Amazon CloudWatch to track and monitor user activity, helping to detect and respond to security incidents.
Implement least privilege access: Grant users, groups, and roles the minimum permissions necessary to perform their tasks and review these permissions regularly to ensure they remain appropriate.
<a name="organisation-scp"></a>
AWS Organizations and Service Control Policies (SCPs)
AWS Organizations enables you to manage and consolidate multiple AWS accounts centrally. With Organizations, you can apply consistent policies across your accounts, simplifying administration and reducing the risk of misconfigurations. Service Control Policies (SCPs) are a powerful tool within AWS Organizations that allow you to define the full permissions for all users and roles within an organization or organizational unit (OU).
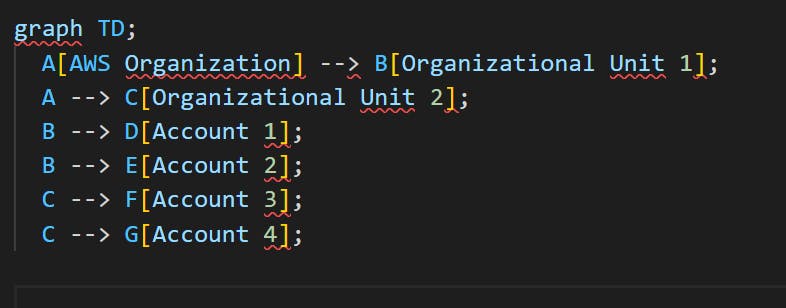
Here's an example of a mermaid diagram illustrating the hierarchy within an AWS Organization:
<a name="monitoring-auditing"></a>
Monitoring and Auditing IAM
To maintain the security and compliance of your AWS environment, monitoring and auditing IAM activities is essential. AWS provides several tools to help you track and analyze IAM usage:
AWS CloudTrail: This service records API calls for your account, including IAM actions, and delivers log files to a specified S3 bucket. You can use CloudTrail logs to identify unauthorized access, troubleshoot issues, and maintain compliance.
Amazon CloudWatch: CloudWatch monitors your AWS resources and applications in real-time, allowing you to set alarms and receive notifications based on specific events or metrics. You can use CloudWatch to detect abnormal activity, such as an unusually high number of failed login attempts.
AWS Config: This service continuously tracks and records changes to your AWS resources, including IAM policies, roles, and users. You can use AWS Config to assess your resource configurations and ensure compliance with security policies.
Conclusion
AWS Identity and Access Management (IAM) is an essential service that helps you manage access to your AWS resources securely. By following the best practices and leveraging the various IAM components and policy types, you can create a robust security posture for your AWS environment.
Monitoring and auditing IAM activities are crucial to maintaining security and compliance, and AWS provides various tools to support these efforts. With a strong understanding of IAM, you can effectively control access to your resources and keep your AWS infrastructure secure.
